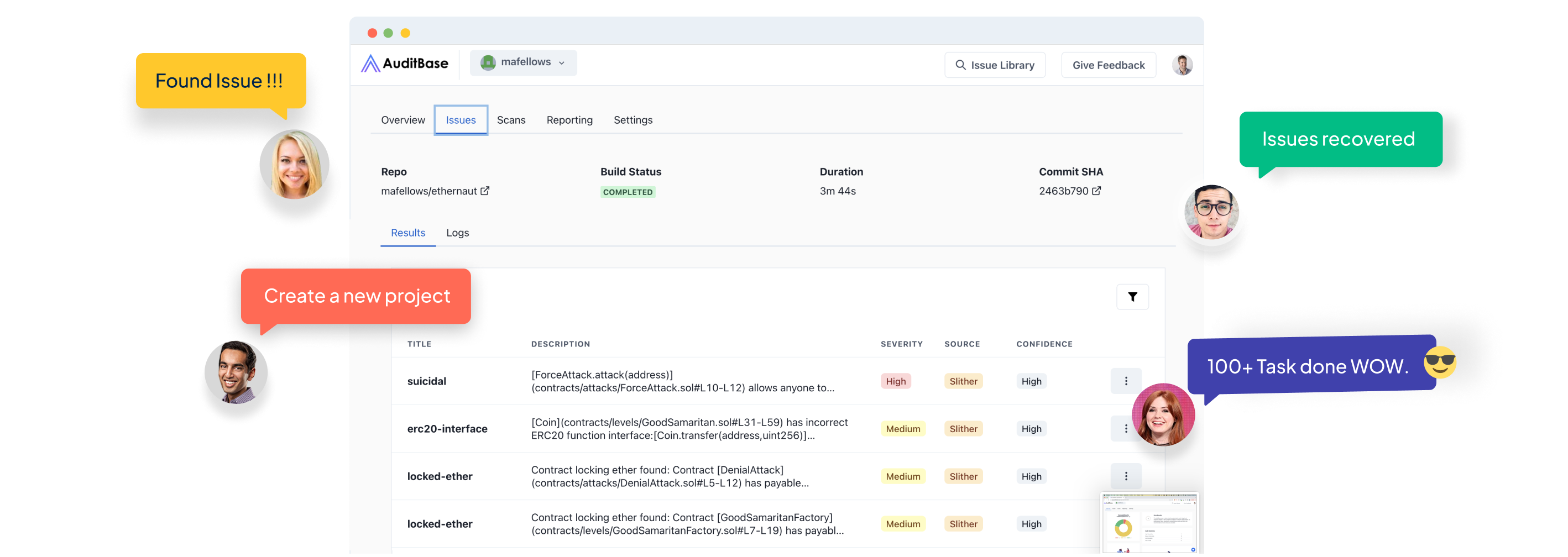
Threat detection and issue management for smart contract development teams.
Analyze code and integrate directly with source control to trigger the audit every time developers push code.
AuditBase has been battle-tested to find over 400 types of issues. Our team is adding new vulnerabilities weekly.




Looking to save your users some gwei? AuditBase recommends easy-to-implement changes. We'll also estimate how much your users will save



AuditBase is an easy-to-use application for developers, investors, and protocol stakeholders. Whether your contract is already deployed or still in development, our platform makes it easy to analyze Solidity code.




AuditBase has been battle-tested to find over 400 types of issues. Our team is adding new vulnerabilities weekly.
In the ever-evolving world of blockchain technology, security remains a top priority for developers and users. With the rise of smart contracts, ensuring the safety and integrity of these self-executing digital agreements has become essential.
This is why we've built AuditBase to be one of the leading solidity audit tools. AuditBase is designed to thoroughly examine the code of a smart contract and identify any potential vulnerabilities or flaws.
By conducting a smart contract audit, developers can gain confidence in the security of their code and protect against potential attacks. Unfortunately, smart contract audits are typically expensive and time-consuming.
Although you should absolutely get a smart contract audit from a reputable auditor, it's important to catch as many issues as you can quickly.
Security auditors use a variety of techniques such as symbolic execution and dynamic analysis to identify vulnerabilities and suggest improvements. They provide valuable feedback on the contract's structure, function, and ownership.
AuditBase has developed the most extensive scanning solution on the market. AuditBase competes in Code4rena bot races and is trusted by some of the top solo auditors and audit firms in the space.
Deploying smart contracts without conducting a proper audit can lead to loss of funds, breaches in contract security, and damage to the reputation of the project.
Although Auditbase cannot detect all issues, automated Solidity audit tools like AuditBase play a crucial role in the developing Web3 ecosystem.
When it comes to securing your smart contracts, using leading solidity audit tools can provide numerous features and benefits. These tools offer advanced smart contract analysis capabilities, ensuring that your code is thoroughly examined for potential vulnerabilities and flaws.
contract code. They can identify common vulnerabilities such as reentrancy attacks or uninitialized storage variables, allowing you to address these issues before deploying your smart contract. This not only protects the integrity of your code but also prevents potential attacks and loss of funds.
Another benefit of using solidity audit tools is the detailed analysis report they provide. These reports offer a comprehensive overview of the security of your smart contract, highlighting any potential issues found. This allows you to understand the specific vulnerabilities and flaws in your code, making it easier for you to make the necessary improvements.
Additionally, these audit tools can provide insights into the ownership of your smart contract. They can analyze the contract address and ensure that the correct parties have access rights and permissions. This helps to prevent unauthorized changes to the contract and enhances the overall security of your smart contract.
By using leading solidity audit tools, you can have peace of mind knowing that your smart contract has undergone a thorough security analysis. This not only protects your code but also safeguards the funds and reputation associated with your project. So, take advantage of these tools to ensure the safety and integrity of your smart contracts.
Solidity audit tools like AuditBase play a vital role in improving the security of smart contracts and ensuring the integrity of the code. By thoroughly analyzing the smart contract code, these tools can identify potential vulnerabilities and flaws, allowing developers to address them before deploying the contract on the blockchain. This is essential for protecting against potential attacks, loss of funds, and damage to the reputation of the project.
One important aspect that solidity audit tools help with is the analysis of the smart contract address. By verifying the ownership and access rights of the contract, these tools can prevent unauthorized changes and enhance the overall security of the contract. This is crucial for maintaining the integrity of the contract and ensuring that only the correct parties have control over it.
In addition, solidity audit tools provide detailed analysis reports that highlight any potential security issues found in the code. This allows developers to gain a deeper understanding of the vulnerabilities and flaws present in their smart contract, enabling them to make the necessary improvements.
By utilizing solidity audit tools, developers can significantly enhance the security of their smart contracts, giving both themselves and their users peace of mind. These tools are a crucial component of the smart contract development process and should not be overlooked.
There are a few different automated tools available. Some are free, and others are paid.
Some of the most common tools that developers currently use are Slither and MythX.
Slither is an excellent open-source tool that will analyze solidity smart contracts for common issues. However, Slither can be difficult to configure, can throw many false positives, and does not have nearly as many detectors as AuditBase. Slither also does not generate reports that you can share with other team members.
We absolutely recommend you run Slither since it is a free tool. However, it doesn't support enough issue detectors in order to provide an additional layer of security.
MythX is also a paid tool based on the Mythril open-source security tool.
MythX uses a combination of static and dynamic analysis techniques to examine the code and detect security vulnerabilities. MythX provides a detailed analysis report that includes a list of potential issues, such as reentrancy attacks or uninitialized storage variables, along with suggestions for remediation.
While MythX does generate reports, it can be quite expensive to run. Also, it does not provide particularly useful issue detection in most cases. Many of the issues have to do with the use of `block.timestamp` and it quite frequently throws false positives.
SolidityScan is another tool that generates reports similar to AuditBase. Comparing the two, AuditBase is much more trusted by the auditor community, more cost-effective, and detects more issues.
AuditBase generates QA and gas optimization reports whereas SolidityScan does not.
Also, AuditBase supports ethereum smart contracts as well as other EVM chains. Any Solidity code can use AuditBase's sophisticated set of analysis algorithms to identify potential security vulnerabilities.
The AuditBase report is an easy-to-understand document that highlights any security issues found, allowing developers to quickly address them.
Additionally, AuditBase is a powerful solidity audit tool that focuses on analyzing smart contracts during the development lifecycle. It offers a comprehensive analysis of contract ownership, ensuring that the correct parties have the necessary access rights and permissions.
These are just a few examples of the many solidity audit tools available to developers. Each tool offers its own unique set of features and benefits, so it's important to choose the one that best suits your specific needs and requirements.
View the complete comparison of these tools in the following chart:

When it comes to choosing the right solidity audit tool for your smart contract, there are a few practical tips that can help guide your decision.
Firstly, consider the specific features and functionalities that you require for your project. Some tools specialize in certain types of analysis, such as vulnerability detection or contract ownership analysis. Assess your needs and choose a tool that aligns with them.
Next, consider the user-friendliness and ease of integration of the tool. Look for tools that have a simple and intuitive user interface, as well as clear documentation and support resources. Additionally, consider whether the tool integrates well with your existing development environment. A seamless integration can save you time and effort in the long run.
It is also important to consider the reputation and reliability of the audit tool. Look for reviews and testimonials from other developers who have used the tool. Consider factors such as the tool's track record of identifying vulnerabilities accurately and providing actionable recommendations.
Lastly, take into account the cost of the audit tool. While there are free and open-source tools available, paid tools often offer more comprehensive features and support. Evaluate your budget and choose a tool that provides the best value for your investment.
By considering these practical tips, you can make an informed decision and choose the right audit tool for your given smart contract. This will ensure that your code is thoroughly analyzed for vulnerabilities and flaws, enhancing the overall security of your smart contract.
Right now, AuditBase is offering unlimited scans on the Developer and Professional plans.